28 September 2021 | 10-minute read
Despite the rapid progression of digital services over the last 20 years or so, many insurance policies are still “silent” on whether cyber risks are specifically covered or excluded. Lloyd’s Bulletin Y5258 (July 2019), imposed a requirement on Lloyd’s underwriters to introduce policy language clarifying the treatment of cyber risks. The initial roll-out was for property and other first-party/physical damage classes of business at 1/1/2020, with the remainder of the market staggered over three additional phases. The final phase is now upon us at 1/7 and we have recently published our final batch of model cyber clauses (for the casualty reinsurance market), completing our initial suite.
It would have been resource-intensive, expensive and potentially chaotic for customers if our members all attempted to produce their own cyber clauses from scratch; producing a suite of model cyber clauses, using a common framework and definitions, was clearly a job for the LMA. This has been an exceptionally challenging project, both in terms of complexity and logistics. The team had strong suspicions on the outset that this would be a long and difficult task, with many problems. We were right! However, I am delighted that we have completed our work on time, having produced over 100 model clauses, addressing cyber risks in over 70 lines of business, written under 175 different Lloyd’s risk codes.
Cyber exposures and the interplay with insurance products is extremely complicated. Much relies on interpretation, not least because many areas of insurance have not experienced large numbers of cyber claims and so the market’s understanding of the risks and circumstances is still developing. Even seeking to affirm coverage can be fraught with difficulty; if you use defined terms, there is a potential risk that an unforeseen event might fall outside a definition. If you try to describe coverage very broadly but without defining terms, the meaning becomes inexact and the insurer risks the wording being interpreted against them. Very tricky.
Evolved Process for producing model cyber clauses
Looking back over the past 2 years or so, the LMA Underwriting Team has evolved the process for producing cyber clauses; a combination of our long-standing approach to model wordings production with a new added touch of Socratic method (!):
1. Review potential/actual cyber exposures and loss scenarios
This is actually the most complicated bit of the process; talking through the widest possible range of potential cyber risks faced by an insured and thinking about whether any losses arising might lead to a valid insurance claim.
For example, the classic professional indemnity (PI) risk of “a briefcase left on a train” now becomes a laptop or smartphone left on a train. Is this a cyber event? Could or would this scenario produce a loss under a PI policy giving cover for professional negligence or civil liability? What about where an insured providing professional services (e.g. a law firm) was itself the victim of a cyber-attack, causing a system failure which resulted in a financial loss for a client, such as the collapse of a property sale due to the insured law firm failing to execute a transaction on time? PI coverage would usually be triggered by an act of negligence; is the insured negligent in this scenario, or otherwise exposed due to a contractual or civil liability? These scenarios take some considerable thinking about!
We have been very fortunate in that we have developed our clauses in conjunction with talented underwriters, legal counsel and wordings professionals, all on hand to help us think these issues through and agree on the best approach, or the best set of options. (NB Ultimately it is for the contracting parties to agree terms; our clauses are published for guidance and information only).
2. Consider how typical current policy wordings might respond to cyber events; is the position clear in terms of coverage or exclusion? Is that position acceptable?
In the vast majority of cases, when we started this exercise most existing wordings were totally silent on cyber coverage. Unclear, therefore, on cyber exposures? Many insurance policies, especially casualty and specialty risks, are sold on an “all risks” basis, meaning that articulating coverage for cyber-caused losses in policy wordings is problematic. Given the policy could be triggered by any risk (subject to the limits of the policy), why would you make specific reference to one cause of loss (and in doing so, confuse the client!)? We have attempted to develop methods of doing just this, but it is still ironic that an approach intended to bring clarity sometimes causes confusion. Underwriters and brokers are still working hard on this issue, trying to explain coverages to clients and ensure that the contractual position is nailed down to everyone’s satisfaction. Work in progress!
NB We often found, in discussion, that a cyber event was really just a new trigger of existing coverage, as per the example given above re losing a laptop. Most likely the third party losses would be covered, to some extent, and the fact that a laptop was lost, rather than a set of paper documents, is almost immaterial to the coverage (usually for “civil liabilities, negligent acts, errors or omissions” in this instance).
3. In the context of a model clause; what coverage should be granted, and what should be excluded?
NB The LMA operates within the confines of competition law at all times, so our focus is always on model clauses, not the commercial environment or any live risks.
We formed working groups with our business panels to develop model clauses specific to their market and products, but we used a commonly agreed framework of clause structures and definitions. This approach has allowed us to produce suites of clauses attuned to all of the major product groups, with consistency of structure and terms. The intention is that the consistency will make different clauses easier for all parties to understand, as the clauses and definitions will be the same across the entire suite. (It is not in anyone’s interest to have a thousand different ways of defining the same cyber event). It certainly made it easier to construct clauses for new lines of business as the project progressed. One area of difficulty was where existing clients have their own preferred definitions which differ from ours; we decided (collectively) to stick to our guns, and to leave underwriters to amend clauses and definitions to suit the specific circumstances of the risk.
Our comprehensive definitions of cyber-related matters/circumstances, include*:
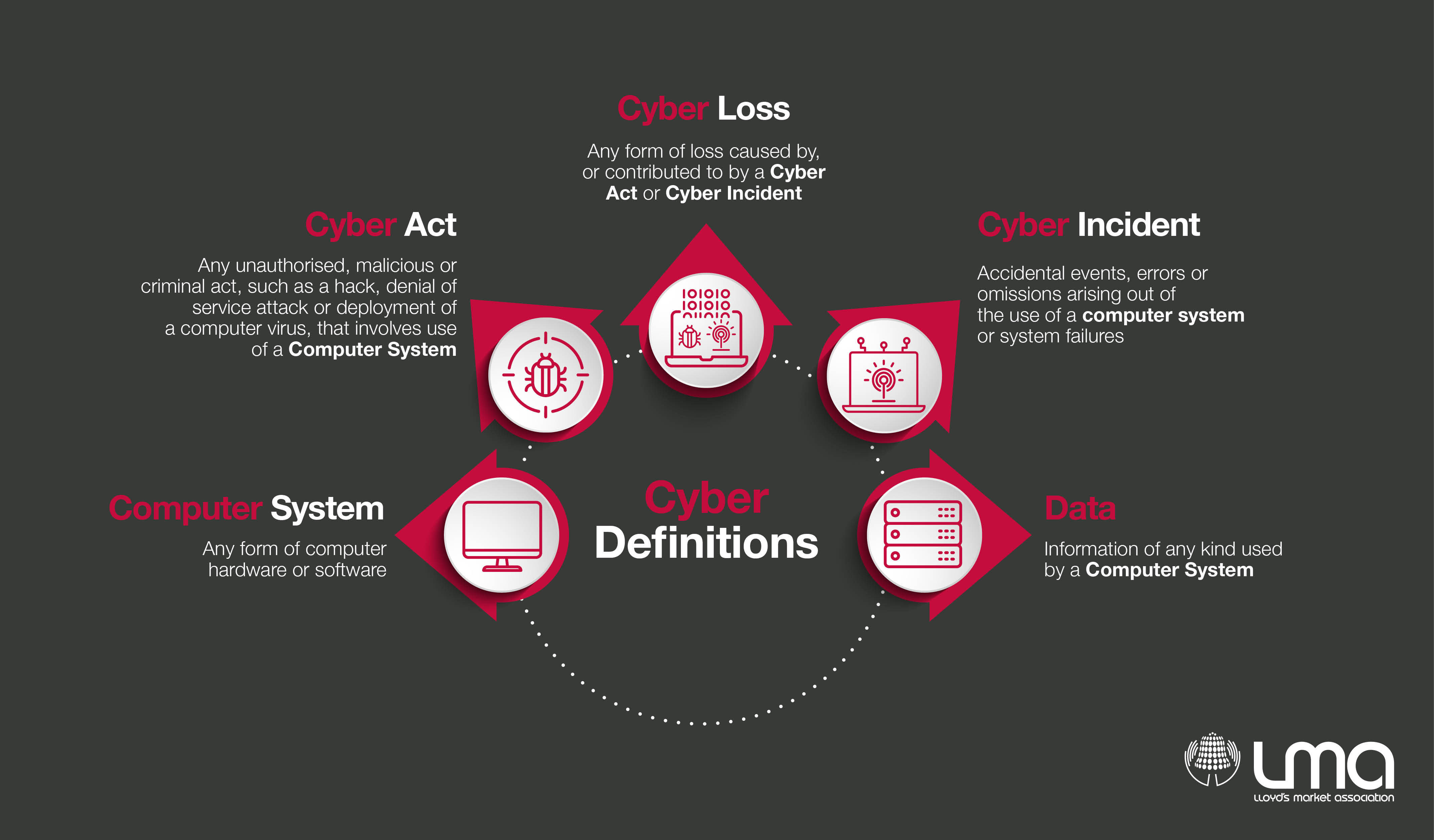
Click here to download the above Cyber Definitions.
These terms, developed after extensive consultation with various LMA members and external Counsel, give us the building blocks of our cyber clauses and are sufficiently broad and comprehensive that they will not need updating for a considerable period of time (we hope!).
*NB Examples/extracts of the above defined terms are provided for information only – please contact the LMA or refer to a published LMA cyber clause (e.g. LMA5400) for these definitions in full.
4. What approach has been used in existing wordings/clauses?
Whilst rare, a number of markets already had some cyber language in place, although some of these clauses date back nearly 20 years or so. It is always a delight to find an old clause that does the job, saving work. However, in most cases the clauses have needed updating, mainly because the Lloyd's requirements go further than the scope of older cyber clauses. Specifically, Lloyd's requires clarity on coverage of first and third party exposures, as well as accidental and deliberate cyber events. So, a clause that grants or excludes coverage for third party risks (for example), but is silent on first party risks, does not do the job unless these other issues are also addressed.
5. Draft the clause(s)
The drafting needs to exactly reflect the underwriting intentions, whether this is a comprehensive grant of coverage, a total exclusion or (perhaps more likely) somewhere in between. The most common model cyber clauses that we have produced are affirmations; clauses that seek to confirm cyber coverage is provided, in line with existing grants of cover and existing limitations of the policy. i.e. If a cyber event triggers (existing) coverage under this policy, then (of course) the policy will respond. Many of our model clauses start with a total cyber exclusion in paragraph one, and then write back the specific cover required in paragraph 2 (and 3, 4 and 5 in some cases!). This approach gives a high level of clarity about what is covered and what is excluded.
In terms of the actual drafting, many hands make light work and it is an iterative process. The LMA has established tried and tested layers of scrutiny for any model clause and whilst this can be laborious it means that lots of different people, including both subject matter experts and wordings professionals all review the clause and suggest changes and improvements where necessary. Our clauses may not be perfect, but all users can rest assured that they have been ruthlessly scrutinised!
6. Test draft against scenarios and revise
As part of the drafting process, it is vital to test the words against different loss scenarios and take a view on whether or not you end up in the right place. Is it clear enough (e.g., could a sentence or expression be interpreted in a different way that conflicts with the intention?). Does the clause enable the payment of claims that you would expect to pay? Ultimately there is only one real test; does the clause respond as expected in the event of a claim?
Typically, the LMA process involves wide consultation and we revise our drafting based on feedback (where appropriate). Consultees might include:
- Other committees or other underwriters in same or related lines of business.
- Wordings professionals.
- Brokers/clients
- Reinsurers/cedants (as appropriate).
- Counsel (internal or external, or both).
8. Hit a deadline and publish!
We do not have infinite time and resources to product perfect model clauses (and no such thing exists in any case). We take a pragmatic approach; a starting point is better than nothing and highly nuanced positions are best left to commercial negotiations that can address the specific circumstances of the risk. We know that it can be frustrating for individual parties when we don’t adopt a specific approach that they advocate. Ultimately our clauses are approved by committee and this process inevitably requires a certain amount of compromise.
Final thought: Within the Lloyd’s market our clause language and model definitions have become the focal point of the debate; the extent to which specific cyber risks exist, how these risks might be addressed and where the risks ought to lie between client, insurer and reinsurer. In this context it is inevitable that not everyone has agreed with the approach we have suggested. Already we have seen many alternative drafts and approaches proposed by brokers, clients and other insurers. They are all innovative and helpful to see, giving options to the contracting parties. Sometimes the drafting we have seen attempts to solve one problem but introduces others; wrestling with perils that remain largely conceptual (if not intangible) is not easy. We acknowledge that some further work may be required to refine and update our suite. In fact, it is not uncommon that we get requests to make changes on a clause before the ink is dry on the original version! As the picture develops and more nuanced commercial positions are required, we will review, reconsider, refine and republish.
At the outset of this journey we were mindful that the “PRA expects that all Solvency II firms that are materially exposed to these risks understand the continuously evolving cyber landscape and demonstrate a continued commitment to developing their knowledge of cyber insurance underwriting risk. This extends to both affirmative and non-affirmative elements of cyber risk.”
We think that as part of this wordings process, we have helped to develop that knowledge considerably.
David Powell
Head of Technical Underwriting